Here you can find a proxy script that can help you to intercept your inverters logging.
Be aware that with interception the logging is no longer delivered to the logging servers in the cloud unless you redirect it again to the Solarman logging servers.
How interception works
By rerouting trafic for ‘176.58.117.69’ to the host running omnikloggerproxy.py and using Network Address Translation, you can simulate the logger server and process to logger data.
The rerouting can to be done at the routing device that is the default gateway for the inverter. I am using a Fritz!Box .
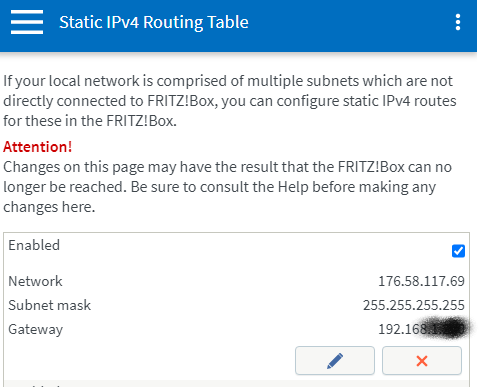
Rerouting can be configured by adding a static routing rule for 176.58.117.69 to the internal ip adress of the host running the NAT rules and the omnikloggerproxy.py script.
Example adding static route on Fritz!Box:
See the comments in the example script for more details. Note: Using iptables on a Synology NAS if not officially supported. The nas might reload the iptables during updates or security checks. An option is to make a second script that runs daily before sunrise that reloads the iptables to ensure the Network Address Translation is performed.
An example (bash) for the iptables rules to configure:
#! /bin/bash LOCAL_IP="192.168.1.x" DEST_PORT="10004" OMNIK_LOGGER_ADDRESS="176.58.117.69" # Flush existing NAT rules iptables -t nat -F OUTPUT iptables -t nat -F PREROUTING # Set NAT RULES correctly iptables -t nat -A PREROUTING -p tcp -d $OMNIK_LOGGER_ADDRESS --dport $DEST_PORT -j DNAT --to-destination $LOCAL_IP:$DEST_PORT iptables -t nat -A OUTPUT -p tcp -d $OMNIK_LOGGER_ADDRESS -j DNAT --to-destination $LOCAL_IP
Adjust LOCAL_IP to the IP address of the host in your internal network that is used for the rerouting.
If you have an unused Raspberry PI or some othe devive that can run Linux, my advise would be to use that device for interception the logger traffic, to avoid conflicts on your Synology.
Still forward the logging to Omnik portal
The omnikloggerproxy.py script enables you to intercept the logger data, send it to MQTT and still forward your data to the logging servers in the cloud. There only problem is that by rerouting trafic to ‘176.58.117.69’ will also prevent forwarding. This way you will not get any updates forwarded to the SolarMan services. If you have the possibility to run omnikloggerproxy.py on a host elsewhere on the Internet, you could still forward your inverters logging to that host and finally proxy the logging to the SolarMAN portals. This scenario is supported. The second instance of omnikloggerproxy.py will then forward to 176.58.117.69:10004 over TCP so it will be delivered to the Solarman infrastructure and will become available in https://www.solarmanpv.com/portal.
